Microcontroller adds strong security to larger systems
MOYA-TECH 2022-05-19
Microchip has announced a cyber-attack-resilient microcontroller family for securing end-user equuipment that goes “beyond NIST 800-193 Platform Firmware Resiliency guidelines with run-time firmware protection that anchors the secure boot process while establishing an entire chain-of-trust for the system”, according to the company, adding that it is also designed for Open Compute Project Security
Called CEC173x, the aim is to be a real-time root-of-trust for servers, telecoms, networking and industrial equipment.
To do this, the MCU is inserted between application’s main processor and the flash memory that stores the main application code, and manages the security of that stored code including protecting it during up-dates.
Caveat: Electronics Weekly worked with the limited information available to create this article, and errors might have crept in – Microchip has been asked to check it.
The MCU also interveins in the application processors I2C bus or SMBus to reduce the changes of hacking through those channels.
Its on-die processor is a 32bit 96MHz Arm Cortex-M4 with an embedded boot ROM to store the power on/boot sequence and APIs available during run time.
“When VTR_REG power is applied to the device, the secure boot loader API is used to download the firmware image from internal flash storage,” said Microchip. “Programming capability for this flash is provided by various means, allowing system designers to customise the device’s behavior while maintaining the integrity of the image by cryptographic signatures.”
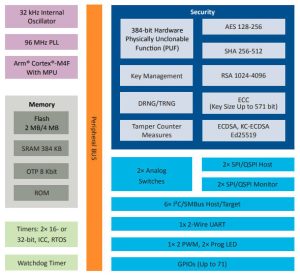
On-chip security resorces include a 384bit physically unclonable function (PUF) for root key and symmetric secret and private key generation, a true random number generator, an encryption engine (AES128, AES192, AES256, SHA-2, SHA-256, SHA-512, RSA-1024 to RSA-4096, ECDSA, EC-KCDSA, Ed25519) and a key management engine.
Device and firmware attestation is provided and there are (unspecifierd) side-channel attack countermeasures, according to Microchip.
“The attestation feature provides trustworthy evidence to ensure that critical devices in the platform are authentic,” it said. “Life-cycle management and ownership transfer features protect secrets throughout the end product lifecycle and during the transfer of product ownership, allowing different operators to use the system platform securely without compromising information.”
The CEC1736 product page can be found here and there is an associated development board, as well as the company’s Trust Platform Design Suite (TPDS)and its Soteria-G3 firmware.
